In the digital age, where data breaches and cyber threats loom large, the guardians of the virtual realm are the unsung heroes of the modern world the cybersecurity experts. 🛡️💻
Imagine a world where your skills are in constant demand, where your expertise in safeguarding digital fortresses can take you to unprecedented heights.
Welcome to the captivating universe of elite cybersecurity careers! 🌐✨
From the ingenious minds who thwart hackers at every turn to the architects building impenetrable virtual citadels.
This is the realm where audacious problem solvers thrive and cutting-edge technology meets unyielding resolve.
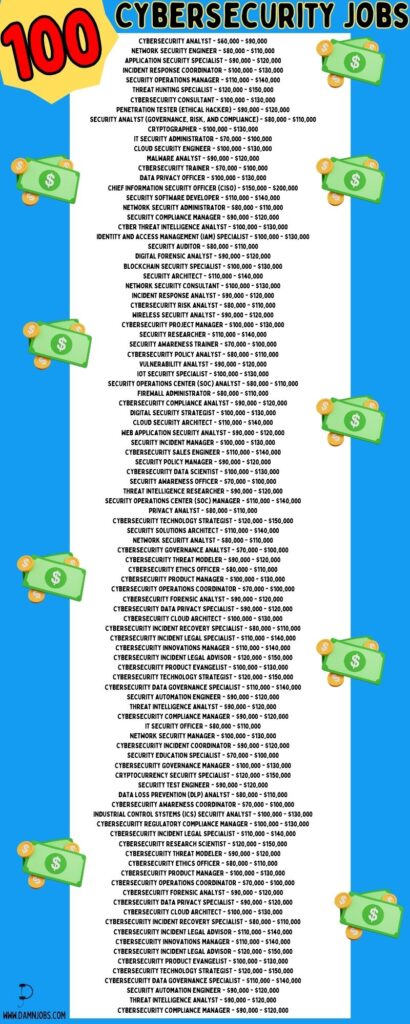
In this exhilarating journey, we unveil 100 exceptional cybersecurity roles that promise not just job titles, but gateways to a future where every click of your keyboard shapes a secure world.
Are you ready to decode the secrets of success in the digital age? Let’s take the plunge into the captivating world of elite cybersecurity careers!
1. Cybersecurity Analyst:
A Cybersecurity Analyst plays a critical role in safeguarding an organization’s digital assets by monitoring and analyzing security systems to identify vulnerabilities and threats.
They conduct security assessments, manage intrusion detection systems, and respond to incidents promptly.
On average, Cybersecurity Analysts earn around $80,000 to $100,000 per year.
Key certifications for this role include CompTIA Security+, Certified Information Systems Security Professional (CISSP), and Certified Ethical Hacker (CEH). The job process involves continuous monitoring of security systems, identifying and addressing security gaps, conducting vulnerability assessments, and collaborating with IT teams to implement effective security measures.
Example Job Process:
- Vulnerability Assessment: Run regular scans to identify vulnerabilities in the organization’s network and systems.
- Threat Detection: Monitor security logs and alerts for signs of unauthorized access or suspicious activities.
- Incident Response: Analyze security incidents, determine the extent of the breach, and take immediate action to mitigate risks.
- Security Patching: Apply security patches and updates to ensure systems are up to date and protected.
- Security Awareness Training: Educate employees about cybersecurity best practices to minimize human-related risks.
2. DevSecOps Engineer:
A DevSecOps Engineer focuses on integrating security into the software development lifecycle. They collaborate with development and operations teams to ensure that security practices are embedded into the entire process. DevSecOps Engineers earn an average salary of $110,000 to $130,000 per year. Pertinent certifications for this role include Certified DevSecOps Professional (DPS) and Certified Information Systems Security Professional (CISSP). The job process involves automating security processes, implementing security controls in CI/CD pipelines, conducting vulnerability assessments, and providing expert guidance on secure coding practices.
Example Job Process:
- Secure CI/CD Pipeline: Integrate security tools to scan code for vulnerabilities as it is developed and deployed.
- Automated Testing: Implement automated security testing to identify vulnerabilities early in the development process.
- Infrastructure as Code: Apply security controls to infrastructure scripts, ensuring secure cloud deployments.
- Incident Response Integration: Design incident response processes within the CI/CD pipeline to address security incidents quickly.
- Secure Coding Review: Collaborate with developers to review code for security vulnerabilities and provide guidance.
3. Media Exploitation Analyst (Cyber Crime Investigator):
A Media Exploitation Analyst is responsible for extracting digital evidence from various media formats, aiding in cybercrime investigations. They work closely with law enforcement agencies and legal teams to support legal proceedings. The average salary for this role ranges from $70,000 to $90,000 per year. Relevant certifications include Certified Digital Forensics Examiner (CDFE) and Certified Cyber Crime Investigator (CCCI). The job process includes analyzing digital media, recovering deleted files, preparing detailed reports, and providing expert testimony in court.
Example Job Process:
- Digital Evidence Extraction: Analyze images, videos, and audio recordings to uncover hidden evidence.
- Deleted File Recovery: Utilize forensics tools to recover deleted files and metadata from devices.
- Legal Collaboration: Work with law enforcement agencies to gather evidence for legal cases.
- Expert Testimony: Provide expert testimony in court, explaining the technical aspects of digital evidence.
- Evidence Documentation: Prepare comprehensive reports detailing findings and evidence in a clear manner.
Each of these roles showcases the diverse opportunities within the cybersecurity field, highlighting the crucial nature of cybersecurity professionals in safeguarding digital assets, responding to incidents, and contributing to the overall security posture of organizations. Remember that job titles, responsibilities, salaries, and required certifications can vary based on location, industry, and organization size.
4. Vulnerability Researcher & Exploit Developer:
A Vulnerability Researcher & Exploit Developer focuses on identifying security vulnerabilities in software and systems and developing proof-of-concept exploits to demonstrate their potential impact. They play a crucial role in strengthening software security. The average salary for this role ranges from $100,000 to $120,000 per year. Key certifications include Certified Ethical Hacker (CEH) and Offensive Security Certified Professional (OSCP). The job process includes analyzing software, discovering vulnerabilities, creating exploits, and collaborating with development teams to remediate weaknesses.
Example Job Process:
- Software Analysis: Analyze software applications to identify potential security vulnerabilities.
- Vulnerability Discovery: Use various tools and techniques to discover vulnerabilities in the software.
- Exploit Development: Develop proof-of-concept exploits to demonstrate the potential impact of vulnerabilities.
- Collaboration with Developers: Work closely with development teams to provide recommendations for vulnerability mitigation.
- Security Enhancement: Contribute to enhancing security measures and best practices within the development process.
5. Security Awareness Officer (Security Awareness & Communications Manager):
A Security Awareness Officer focuses on promoting a strong cybersecurity culture within an organization by creating and implementing security awareness programs. They educate employees about cybersecurity best practices to reduce human-related risks. The average salary for this role ranges from $90,000 to $110,000 per year. Pertinent certifications include Certified Security Awareness Practitioner (CSAP) and Certified Information Systems Security Professional (CISSP). The job process involves designing security awareness campaigns, conducting training sessions, and collaborating with cross-functional teams.
Example Job Process:
- Campaign Design: Develop engaging security awareness campaigns using various communication channels.
- Training Sessions: Conduct training sessions to educate employees about phishing, social engineering, and other risks.
- Content Creation: Create informative materials such as posters, newsletters, and videos to promote cybersecurity awareness.
- Metrics and Assessment: Measure the effectiveness of awareness campaigns and adjust strategies as needed.
- Collaboration: Collaborate with IT, HR, and management teams to ensure consistent messaging and engagement.
Remember that these job roles are just a glimpse of the diverse opportunities within the cybersecurity field. Each role serves a unique purpose in enhancing the overall security posture of organizations, whether it’s identifying vulnerabilities, securing software development processes, investigating cybercrimes, or promoting cybersecurity awareness. The field continues to evolve with the ever-changing digital landscape, offering professionals rewarding careers and the chance to contribute to the protection of sensitive information and critical systems.
6. Cloud Security Analyst:
A Cloud Security Analyst specializes in securing cloud environments, ensuring the confidentiality, integrity, and availability of data stored and processed in the cloud.
They assess cloud architecture, configure security controls, and monitor for cloud-specific threats. The average salary for this role ranges from $100,000 to $120,000 per year. Key certifications include Certified Cloud Security Professional (CCSP) and Certified Information Systems Security Professional (CISSP). The job process includes assessing cloud security, configuring access controls, implementing encryption, and providing incident response in the cloud environment.
Example Job Process:
- Cloud Assessment: Evaluate the security posture of cloud infrastructure and services.
- Access Control: Configure role-based access controls (RBAC) and ensure least privilege access.
- Encryption Implementation: Implement encryption for data at rest and in transit within the cloud.
- Threat Monitoring: Monitor cloud logs and alerts to detect and respond to cloud-specific threats.
- Incident Response: Investigate and respond to security incidents occurring within the cloud environment.
7. Intrusion Detection / SOC Analyst (Cyber Defense Analyst):
An Intrusion Detection Analyst, also known as a Security Operations Center (SOC) Analyst, monitors network and system activity for signs of unauthorized access and potential security incidents. They play a crucial role in identifying and responding to security threats in real-time. The average salary for this role ranges from $80,000 to $100,000 per year. Key certifications include Certified Intrusion Analyst (GIAC), CompTIA Security+, and Certified Information Systems Security Professional (CISSP). The job process involves real-time monitoring of network traffic, analyzing security alerts, investigating incidents, and coordinating incident response efforts.
Example Job Process:
- Real-time Monitoring: Monitor network traffic and security alerts using intrusion detection systems.
- Alert Analysis: Analyze alerts to determine their severity and potential impact on the organization.
- Incident Investigation: Investigate security incidents, gather evidence, and determine the root cause.
- Incident Response: Coordinate with incident response teams to mitigate threats and vulnerabilities.
- Post-Incident Analysis: Perform post-incident analysis to identify lessons learned and improve future responses.
8. Chief Information Security Officer (CISO) (Executive Cyber Leadership):
A Chief Information Security Officer (CISO) is a senior executive responsible for establishing and leading an organization’s cybersecurity strategy.
They ensure the organization’s information assets are protected, compliance is maintained, and risks are managed effectively. The average salary for this role ranges from $150,000 to $250,000 or more per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves defining cybersecurity policies, managing security teams, overseeing risk assessments, and providing strategic guidance to senior leadership.
Example Job Process:
- Cybersecurity Strategy: Develop and execute a comprehensive cybersecurity strategy aligned with business goals.
- Policy Development: Establish cybersecurity policies and procedures to ensure compliance and risk mitigation.
- Team Leadership: Lead and manage cybersecurity teams, including incident response, compliance, and engineering.
- Risk Assessment: Conduct regular risk assessments to identify and prioritize cybersecurity risks.
- Board Communication: Present cybersecurity updates and risks to the board of directors and senior executives.
Each of these roles represents a distinct pathway within the cybersecurity field, contributing to the protection of digital assets, sensitive information, and critical systems. As technology continues to advance, the demand for cybersecurity professionals remains strong, making it an exciting and rewarding career choice for those passionate about defending against cyber threats and ensuring a secure digital landscape.
9. OSINT Investigator:
An Open Source Intelligence (OSINT) Investigator specializes in gathering information from publicly available sources on the internet to support various investigations. They play a vital role in collecting relevant data and uncovering insights for cyber threat analysis and other intelligence purposes. The average salary for this role ranges from $70,000 to $90,000 per year. Key certifications include the Certified Cyber Intelligence Professional (CCIP) and Certified Information Systems Security Professional (CISSP). The job process involves data collection from open sources, analyzing information, identifying trends, and providing actionable intelligence to support decision-making.
Example Job Process:
- Data Collection: Gather information from open sources such as social media, websites, and forums.
- Threat Intelligence: Analyze collected data to identify potential cyber threats, trends, and patterns.
- Investigation Support: Provide intelligence to support investigations, incident response, and decision-making.
- Report Generation: Compile comprehensive intelligence reports with actionable insights.
- Continuous Monitoring: Maintain awareness of emerging threats and update intelligence accordingly.
10. Technical Director (Information Systems Security Manager):
A Technical Director in the role of an Information Systems Security Manager oversees the security operations of an organization, ensuring the implementation and management of security measures to protect information assets.
They lead security teams, develop security policies, and ensure compliance with industry standards and regulations. The average salary for this role ranges from $130,000 to $160,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves strategic planning, team management, risk assessment, and ensuring the organization’s security posture is maintained.
Example Job Process:
- Security Strategy: Develop and execute a comprehensive security strategy aligned with organizational goals.
- Policy Development: Establish security policies, standards, and procedures to ensure compliance.
- Team Leadership: Manage security teams, oversee security operations, and ensure skill development.
- Risk Management: Conduct regular risk assessments, identify vulnerabilities, and prioritize mitigation efforts.
- Regulatory Compliance: Ensure the organization’s security practices meet relevant regulations and standards.
As the digital landscape evolves, cybersecurity continues to be a dynamic and critical field.
These job roles demonstrate the diversity of opportunities within cybersecurity, each playing a vital role in protecting data, systems, and infrastructure.
With the increasing reliance on technology and the rise of cyber threats, cybersecurity professionals are essential in preventing, detecting, and responding to security incidents.
Whether you’re drawn to investigative work, technical leadership, cloud security, or risk management, the cybersecurity field offers a wide array of fulfilling career paths that contribute to a safer digital world.
11. Application Penetration Tester (Secure Software Accessor):
An Application Penetration Tester, also known as a Secure Software Accessor, specializes in assessing software applications for security vulnerabilities.
They simulate real-world attacks to identify weaknesses that could be exploited by malicious actors. The average salary for this role ranges from $90,000 to $110,000 per year. Key certifications include Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and Certified Information Systems Security Professional (CISSP). The job process involves identifying application vulnerabilities, performing penetration testing, providing detailed reports, and collaborating with developers to remediate vulnerabilities.
Example Job Process:
- Vulnerability Identification: Analyze software applications to identify potential security vulnerabilities.
- Penetration Testing: Simulate real-world attacks to exploit vulnerabilities and assess their impact.
- Reporting: Document findings and recommendations in comprehensive penetration testing reports.
- Collaboration with Developers: Work closely with development teams to provide guidance on vulnerability remediation.
- Security Enhancement: Contribute to improving secure coding practices and application security measures.
12. Cloud Security Architect:
A Cloud Security Architect designs and implements secure cloud architectures that protect data and applications hosted in cloud environments. They collaborate with stakeholders to ensure cloud solutions meet security and compliance requirements.
The average salary for this role ranges from $130,000 to $150,000 per year. Key certifications include Certified Cloud Security Professional (CCSP), AWS Certified Solutions Architect, and Certified Information Systems Security Professional (CISSP). The job process involves assessing cloud security requirements, designing secure architectures, implementing security controls, and guiding cloud migration efforts.
Example Job Process:
- Requirement Analysis: Collaborate with stakeholders to identify security requirements for cloud solutions.
- Architecture Design: Develop secure cloud architectures that align with industry best practices.
- Security Control Implementation: Implement security controls such as encryption, identity management, and access controls.
- Cloud Compliance: Ensure cloud solutions comply with relevant regulations and standards.
- Cloud Migration Guidance: Provide guidance and support for migrating applications and data to the cloud securely.
13. Security Compliance Manager:
A Security Compliance Manager ensures that an organization adheres to relevant cybersecurity regulations, industry standards, and internal policies. They develop compliance programs, conduct audits, and monitor ongoing adherence to security requirements. The average salary for this role ranges from $110,000 to $130,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), and Certified Information Systems Auditor (CISA).
The job process involves creating compliance frameworks, conducting assessments, implementing controls, and collaborating with legal and regulatory teams.
Example Job Process:
- Compliance Framework Development: Develop compliance frameworks aligned with industry standards and regulations.
- Assessment and Auditing: Conduct regular assessments and audits to ensure adherence to security requirements.
- Control Implementation: Implement security controls and practices to address compliance gaps.
- Documentation and Reporting: Document compliance efforts and provide reports to relevant stakeholders.
- Regulatory Liaison: Collaborate with legal and regulatory teams to address compliance inquiries and requirements.
These roles collectively demonstrate the vast array of opportunities within the cybersecurity field. Each position contributes to the overall security and resilience of digital assets, whether through vulnerability assessment, cloud security design, compliance management, or ethical hacking. As technology continues to advance, the role of cybersecurity professionals remains pivotal in safeguarding sensitive information, critical infrastructure, and digital operations.
14. Cyber Defense Incident Responder:
A Cyber Defense Incident Responder specializes in responding to and mitigating cybersecurity incidents. They play a crucial role in identifying and containing security breaches, investigating the root cause, and restoring normal operations.
The average salary for this role ranges from $90,000 to $110,000 per year. Key certifications include Certified Incident Handler (CIH), Certified Information Systems Security Professional (CISSP), and CompTIA Cybersecurity Analyst (CySA+). The job process involves incident detection, containment, investigation, recovery, and post-incident analysis.
Example Job Process:
- Incident Detection: Monitor systems for signs of potential security breaches and anomalies.
- Incident Containment: Isolate affected systems to prevent further spread of the attack.
- Incident Investigation: Analyze the attack vector, identify compromised data, and assess impact.
- Recovery: Restore systems and services to their normal state while ensuring security.
- Post-Incident Analysis: Conduct a thorough review to identify lessons learned and enhance future incident response.
15. Security Awareness & Communications Manager:
A Security Awareness & Communications Manager focuses on raising cybersecurity awareness among employees and stakeholders. They design and implement security awareness programs and campaigns to educate individuals about security risks and best practices.
The average salary for this role ranges from $80,000 to $100,000 per year. Key certifications include Certified Security Awareness Practitioner (CSAP) and Certified Information Systems Security Professional (CISSP). The job process involves creating awareness programs, developing communication strategies, delivering training, and measuring program effectiveness.
Example Job Process:
- Program Design: Develop engaging security awareness programs and campaigns.
- Communication Strategy: Design effective communication strategies to convey security messages.
- Training Delivery: Conduct training sessions to educate employees about cybersecurity risks.
- Content Creation: Create informative materials such as posters, newsletters, and videos.
- Metrics and Evaluation: Measure the impact of awareness programs and adapt strategies based on feedback.
- 16. Vulnerability Researcher & Exploit Developer (Vulnerability Assessment Analyst):
A Vulnerability Researcher & Exploit Developer in the role of a Vulnerability Assessment Analyst focuses on identifying and assessing security vulnerabilities within systems and applications. They analyze the potential impact of vulnerabilities and provide recommendations for mitigation.
The average salary for this role ranges from $100,000 to $120,000 per year. Key certifications include Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and Certified Information Systems Security Professional (CISSP). The job process involves vulnerability scanning, assessment, impact analysis, reporting, and collaborating with development teams.
Example Job Process:
- Vulnerability Scanning: Conduct automated scans to identify potential security vulnerabilities.
- Vulnerability Assessment: Analyze scan results to determine the severity and impact of vulnerabilities.
- Impact Analysis: Assess the potential consequences of exploiting identified vulnerabilities.
- Reporting and Remediation: Document findings and recommend mitigation strategies.
- Collaboration with Developers: Work with development teams to prioritize and remediate vulnerabilities.
These job roles collectively showcase the diverse opportunities within the cybersecurity field. From incident response and vulnerability assessment to security awareness and communications management, each role contributes to enhancing the security posture of organizations and defending against cyber threats. As technology continues to advance, the importance of cybersecurity professionals in protecting data, systems, and critical infrastructure remains paramount.
17. Media Exploitation Analyst (Cyber Crime Investigator):
A Media Exploitation Analyst, in the role of a Cyber Crime Investigator, specializes in extracting digital evidence from various media formats to support cybercrime investigations. They work closely with law enforcement agencies and legal teams to uncover hidden evidence and contribute to legal proceedings. The average salary for this role ranges from $70,000 to $90,000 per year. Key certifications include Certified Digital Forensics Examiner (CDFE) and Certified Cyber Crime Investigator (CCCI). The job process involves analyzing digital media, recovering deleted files, preparing reports, and providing expert testimony.
Example Job Process:
- Digital Evidence Extraction: Analyze images, videos, and audio recordings to uncover hidden evidence.
- Deleted File Recovery: Utilize forensics tools to recover deleted files and metadata.
- Legal Collaboration: Work with law enforcement agencies to gather evidence for legal cases.
- Expert Testimony: Provide expert testimony in court to explain digital evidence.
- Evidence Documentation: Prepare detailed reports to present findings in a clear manner.
- 18. Technical Director (Information Systems Security Manager):
A Technical Director in the role of an Information Systems Security Manager oversees an organization’s security operations, ensuring the implementation of security measures and adherence to policies. They lead security teams, manage risk, and ensure compliance with industry standards. The average salary for this role ranges from $130,000 to $160,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves strategic planning, team management, risk assessment, policy enforcement, and incident response coordination.
Example Job Process:
- Security Strategy: Develop and execute a comprehensive security strategy aligned with business objectives.
- Team Leadership: Manage security teams, ensuring collaboration and skill development.
- Risk Management: Conduct risk assessments, identify vulnerabilities, and prioritize mitigation.
- Policy Enforcement: Ensure adherence to security policies and industry standards.
- Incident Response Coordination: Oversee incident response efforts, ensuring timely and effective resolution.
19. Cloud Security Analyst:
A Cloud Security Analyst specializes in securing cloud environments, ensuring the confidentiality, integrity, and availability of data and applications. They assess cloud architecture, implement security controls, and monitor for cloud-specific threats. The average salary for this role ranges from $100,000 to $120,000 per year. Key certifications include Certified Cloud Security Professional (CCSP) and Certified Information Systems Security Professional (CISSP). The job process involves cloud security assessment, control implementation, threat monitoring, incident response, and ongoing security enhancement.
Example Job Process:
- Cloud Assessment: Evaluate cloud architecture and services for security vulnerabilities.
- Control Implementation: Configure access controls, encryption, and identity management.
- Threat Monitoring: Monitor cloud logs and alerts for signs of potential threats.
- Incident Response: Investigate and respond to security incidents within the cloud environment.
- Security Enhancement: Continuously improve cloud security measures and best practices.
These roles exemplify the variety of career paths within the cybersecurity field. Whether you’re focused on digital forensics, cloud security, incident response, or strategic leadership, each role contributes to maintaining the integrity, confidentiality, and availability of information in an increasingly interconnected digital world. As cybersecurity threats continue to evolve, the demand for skilled professionals who can protect and defend against these threats remains high.
20. Intrusion Detection / SOC Analyst (Cyber Defense Analyst):
An Intrusion Detection Analyst, also known as a Security Operations Center (SOC) Analyst, plays a critical role in monitoring network and system activity for signs of unauthorized access and potential security incidents. They analyze security alerts, investigate incidents, and coordinate responses to protect the organization’s assets. The average salary for this role ranges from $80,000 to $100,000 per year. Key certifications include Certified Intrusion Analyst (GIAC), CompTIA Security+, and Certified Information Systems Security Professional (CISSP). The job process involves real-time monitoring, alert analysis, incident investigation, response coordination, and post-incident analysis.
Example Job Process:
- Real-time Monitoring: Monitor network traffic and security alerts using intrusion detection systems.
- Alert Analysis: Analyze alerts to determine their severity and potential impact.
- Incident Investigation: Investigate security incidents, gather evidence, and identify root causes.
- Response Coordination: Coordinate incident response efforts to mitigate threats and vulnerabilities.
- Post-Incident Analysis: Perform post-incident analysis to identify lessons learned and improve future responses.
21. Chief Information Security Officer (CISO) (Executive Cyber Leadership):
A Chief Information Security Officer (CISO) is a senior executive responsible for developing and implementing an organization’s cybersecurity strategy. They ensure the organization’s information assets are protected, compliance is maintained, and risks are managed effectively. The average salary for this role ranges from $150,000 to $250,000 or more per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves cybersecurity strategy development, policy establishment, risk management, team leadership, and engagement with senior executives and boards.
Example Job Process:
- Cybersecurity Strategy: Develop and execute a comprehensive cybersecurity strategy aligned with business goals.
- Policy Establishment: Define cybersecurity policies and procedures to ensure compliance and risk mitigation.
- Team Leadership: Lead and manage cybersecurity teams, including incident response, compliance, and engineering.
- Risk Assessment: Conduct regular risk assessments to identify and prioritize cybersecurity risks.
- Board Engagement: Present cybersecurity updates, risks, and strategies to the board of directors.
22. DevSecOps Engineer:
A DevSecOps Engineer focuses on integrating security practices into the software development process. They work closely with development and operations teams to ensure that security measures are built into the entire software development lifecycle. The average salary for this role ranges from $110,000 to $130,000 per year. Key certifications include Certified DevSecOps Professional (DPS) and Certified Information Systems Security Professional (CISSP). The job process involves secure pipeline integration, automated security testing, infrastructure as code security, incident response integration, and secure coding review.
Example Job Process:
- Secure Pipeline Integration: Integrate security tools into the continuous integration and continuous delivery (CI/CD) pipeline.
- Automated Security Testing: Implement automated security testing to identify vulnerabilities during development.
- Infrastructure as Code Security: Apply security controls to infrastructure scripts for secure cloud deployments.
- Incident Response Integration: Design incident response processes within the CI/CD pipeline to address security incidents.
- Secure Coding Review: Collaborate with developers to review code for security vulnerabilities and provide guidance.
These roles encompass a range of responsibilities within the cybersecurity landscape. As technology advances and cyber threats evolve, professionals in these positions play a critical role in protecting digital assets, responding to incidents, and ensuring that organizations remain secure and resilient in the face of emerging challenges.
23. Media Exploitation Analyst (Cyber Crime Investigator):
A Media Exploitation Analyst, in the role of a Cyber Crime Investigator, specializes in extracting digital evidence from various media formats to support cybercrime investigations. They work closely with law enforcement agencies and legal teams to uncover hidden evidence and contribute to legal proceedings.
The average salary for this role ranges from $70,000 to $90,000 per year. Key certifications include Certified Digital Forensics Examiner (CDFE) and Certified Cyber Crime Investigator (CCCI).
The job process involves analyzing digital media, recovering deleted files, preparing reports, and providing expert testimony.
Example Job Process:
- Digital Evidence Extraction: Analyze images, videos, and audio recordings to uncover hidden evidence.
- Deleted File Recovery: Utilize forensics tools to recover deleted files and metadata.
- Legal Collaboration: Work with law enforcement agencies to gather evidence for legal cases.
- Expert Testimony: Provide expert testimony in court to explain digital evidence.
- Evidence Documentation: Prepare detailed reports to present findings in a clear manner. 24.
Technical Director (Information Systems Security Manager):
A Technical Director in the role of an Information Systems Security Manager oversees an organization’s security operations, ensuring the implementation of security measures and adherence to policies. They lead security teams, manage risk, and ensure compliance with industry standards.
The average salary for this role ranges from $130,000 to $160,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves strategic planning, team management, risk assessment, policy enforcement, and incident response coordination.
Example Job Process:
- Security Strategy: Develop and execute a comprehensive security strategy aligned with business objectives.
- Team Leadership: Manage security teams, ensuring collaboration and skill development.
- Risk Management: Conduct risk assessments, identify vulnerabilities, and prioritize mitigation.
- Policy Enforcement: Ensure adherence to security policies and industry standards. Incident Response
- Coordination: Oversee incident response efforts, ensuring timely and effective resolution.
25. Cloud Security Analyst:
A Cloud Security Analyst specializes in securing cloud environments, ensuring the confidentiality, integrity, and availability of data and applications. They assess cloud architecture, implement security controls, and monitor for cloud-specific threats. The average salary for this role ranges from $100,000 to $120,000 per year.
Key certifications include Certified Cloud Security Professional (CCSP) and Certified Information Systems Security Professional (CISSP).
The job process involves cloud security assessment, control implementation, threat monitoring, incident response, and ongoing security enhancement.
Example Job Process:
- Cloud Assessment: Evaluate cloud architecture and services for security vulnerabilities.
- Control Implementation: Configure access controls, encryption, and identity management.
- Threat Monitoring: Monitor cloud logs and alerts for signs of potential threats.
- Incident Response: Investigate and respond to security incidents within the cloud environment.
- Security Enhancement: Continuously improve cloud security measures and best practices.
26. Intrusion Detection / SOC Analyst (Cyber Defense Analyst):
An Intrusion Detection Analyst, also known as a Security Operations Center (SOC) Analyst, plays a critical role in monitoring network and system activity for signs of unauthorized access and potential security incidents. They analyze security alerts, investigate incidents, and coordinate responses to protect the organization’s assets. The average salary for this role ranges from $80,000 to $100,000 per year.
Key certifications include Certified Intrusion Analyst (GIAC), CompTIA Security+, and Certified Information Systems Security Professional (CISSP). The job process involves real-time monitoring, alert analysis, incident investigation, response coordination, and post-incident analysis.
Example Job Process:
- Real-time Monitoring: Monitor network traffic and security alerts using intrusion detection systems. Alert Analysis: Analyze alerts to determine their severity and potential impact.
- Incident Investigation: Investigate security incidents, gather evidence, and identify root causes.
- Response Coordination: Coordinate incident response efforts to mitigate threats and vulnerabilities.
- Post-Incident Analysis: Perform post-incident analysis to identify lessons learned and improve future responses.
27. Security Awareness & Communications Manager:
A Security Awareness & Communications Manager focuses on raising cybersecurity awareness among employees and stakeholders. They design and implement security awareness programs and campaigns to educate individuals about security risks and best practices.
The average salary for this role ranges from $80,000 to $100,000 per year. Key certifications include Certified Security Awareness Practitioner (CSAP) and Certified Information Systems Security Professional (CISSP).
The job process involves creating awareness programs, developing communication strategies, delivering training, and measuring program effectiveness.
Example Job Process:
- Program Design: Develop engaging security awareness programs and campaigns.
- Communication Strategy: Design effective communication strategies to convey security messages.
- Training Delivery: Conduct training sessions to educate employees about cybersecurity risks.
- Content Creation: Create informative materials such as posters, newsletters, and videos. Metrics and Evaluation: Measure the impact of awareness programs and adapt strategies based on feedback.
28. Vulnerability Researcher & Exploit Developer (Vulnerability Assessment Analyst):
A Vulnerability Researcher & Exploit Developer in the role of a Vulnerability Assessment Analyst focuses on identifying and assessing security vulnerabilities within systems and applications. They analyze the potential impact of vulnerabilities and provide recommendations for mitigation.
The average salary for this role ranges from $100,000 to $120,000 per year. Key certifications include Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and Certified Information Systems Security Professional (CISSP).
The job process involves vulnerability scanning, assessment, impact analysis, reporting, and collaborating with development teams.
Example Job Process:
- Vulnerability Scanning: Conduct automated scans to identify potential security vulnerabilities. Vulnerability Assessment: Analyze scan results to determine the severity and impact of vulnerabilities.
- Impact Analysis: Assess the potential consequences of exploiting identified vulnerabilities. Reporting and Remediation: Document findings and recommend mitigation strategies. Collaboration with Developers: Work with development teams to prioritize and remediate vulnerabilities.
29. Application Penetration Tester (Secure Software Accessor):
An Application Penetration Tester, also known as a Secure Software Accessor, specializes in assessing software applications for security vulnerabilities. They simulate real-world attacks to identify weaknesses that could be exploited by malicious actors.
The average salary for this role ranges from $90,000 to $110,000 per year. Key certifications include Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and Certified Information Systems Security Professional (CISSP). The job process involves identifying application vulnerabilities, performing penetration testing, providing detailed reports, and collaborating with developers to remediate vulnerabilities.
Example Job Process:
- Vulnerability Identification: Analyze software applications to identify potential security vulnerabilities.
- Penetration Testing: Simulate real-world attacks to exploit vulnerabilities and assess their impact.
- Reporting: Document findings and recommendations in comprehensive penetration testing reports.
- Collaboration with Developers: Work closely with development teams to provide guidance on vulnerability remediation.
- Security Enhancement: Contribute to improving secure coding practices and application security measures.
30. DevSecOps Engineer:
A DevSecOps Engineer focuses on integrating security practices into the software development process. They work closely with development and operations teams to ensure that security measures are built into the entire software development lifecycle. The average salary for this role ranges from $110,000 to $130,000 per year.
Key certifications include Certified DevSecOps Professional (DPS) and Certified Information Systems Security Professional (CISSP). The job process involves secure pipeline integration, automated security testing, infrastructure as code security, incident response integration, and secure coding review.
Example Job Process:
- Secure Pipeline Integration: Integrate security tools into the continuous integration and continuous delivery (CI/CD) pipeline.
- Automated Security Testing: Implement automated security testing to identify vulnerabilities during development.
- Infrastructure as Code Security: Apply security controls to infrastructure scripts for secure cloud deployments.
- Incident Response Integration: Design incident response processes within the CI/CD pipeline to address security incidents.
- Secure Coding Review: Collaborate with developers to review code for security vulnerabilities and provide guidance.
These roles encompass a wide array of responsibilities within the cybersecurity field. As technology continues to evolve and cyber threats become more sophisticated, these professionals remain essential in protecting digital assets, responding to incidents, and ensuring that organizations remain secure in an interconnected digital landscape.
31. Cybersecurity Consultant:
A Cybersecurity Consultant provides expert advice and guidance to organizations on their cybersecurity strategy, risk management, and compliance efforts. They assess security posture, identify vulnerabilities, and recommend solutions to enhance security.
The average salary for this role ranges from $90,000 to $120,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves conducting security assessments, developing recommendations, assisting with implementation, and providing ongoing advisory support.
Example Job Process:
- Security Assessment: Evaluate an organization’s security measures, identifying strengths and weaknesses.
- Recommendations: Develop tailored recommendations to improve security posture and compliance.
- Implementation Support: Assist with implementing security measures, controls, and best practices.
- Ongoing Advisory: Provide ongoing guidance to ensure sustained cybersecurity improvements.
- Client Engagement: Collaborate closely with clients to address specific security challenges.
32. Cybersecurity Researcher:
A Cybersecurity Researcher focuses on discovering new vulnerabilities, threats, and attack techniques to enhance understanding and defense against cyber threats. They often work in research teams to uncover novel attack vectors and contribute to the development of defensive strategies.
The average salary for this role ranges from $100,000 to $130,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Ethical Hacker (CEH).
The job process involves threat analysis, vulnerability research, experimentation, publication, and collaboration with security communities.
Example Job Process:
- Threat Analysis: Study emerging threats, attack techniques, and vulnerabilities.
- Vulnerability Research: Discover new vulnerabilities in software, hardware, or systems. Experimentation: Develop and test proof-of-concept exploits to validate vulnerabilities.
- Publication: Share findings through research papers, presentations, or security conferences.
- Community Collaboration: Engage with security communities to share insights and learn from peers.
33. Cybersecurity Trainer:
A Cybersecurity Trainer designs and delivers training programs to educate individuals, employees, and teams about cybersecurity best practices, policies, and skills. They play a vital role in raising awareness and building a security-conscious culture within organizations. The average salary for this role ranges from $80,000 to $100,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves curriculum development, training delivery, skill assessment, feedback incorporation, and continuous improvement.
Example Job Process:
- Curriculum Development: Create engaging training materials, modules, and exercises.
- Training Delivery: Conduct interactive training sessions on cybersecurity topics.
- Skill Assessment: Evaluate participants’ understanding through assessments and practical exercises.
- Feedback Incorporation: Incorporate feedback to enhance training content and delivery.
- Continuous Improvement: Stay updated with evolving threats and technologies to refine training programs.
34. Cybersecurity Policy Analyst:
A Cybersecurity Policy Analyst focuses on developing, reviewing, and implementing cybersecurity policies and procedures that align with industry standards and regulations. They ensure organizations maintain compliance and adhere to best practices. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves policy research, drafting, review, implementation planning, and ongoing policy management.
Example Job Process:
- Policy Research: Stay informed about evolving cybersecurity regulations and best practices.
- Policy Drafting: Develop comprehensive cybersecurity policies tailored to the organization’s needs.
- Review and Approval: Collaborate with stakeholders to review and gain approval for policies.
- Implementation Planning: Develop strategies to ensure policies are effectively communicated and enforced.
- Ongoing Policy Management: Continuously update and refine policies to adapt to changing threats and requirements.
35. Cybersecurity Auditor:
A Cybersecurity Auditor evaluates an organization’s security controls, practices, and processes to ensure compliance with regulatory requirements and industry standards. They conduct thorough assessments to identify gaps and recommend improvements.
The average salary for this role ranges from $90,000 to $120,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Auditor (CISA). The job process involves audit planning, control assessment, findings analysis, report generation, and collaboration with stakeholders for remediation.
Example Job Process:
- Audit Planning: Define scope, objectives, and methodologies for cybersecurity audits.
- Control Assessment: Evaluate security controls, policies, and procedures against standards.
- Findings Analysis: Identify vulnerabilities, weaknesses, and areas of non-compliance.
- Report Generation: Document findings, risks, and recommendations in audit reports.
- Remediation Collaboration: Work with stakeholders to address audit findings and enhance controls.
These roles highlight the dynamic nature of cybersecurity careers. From advising organizations on security strategies to conducting research, delivering training, shaping policies, and performing audits, cybersecurity professionals play a vital role in safeguarding digital assets and responding to the evolving landscape of cyber threats.
36. Cyber Threat Intelligence Analyst:
A Cyber Threat Intelligence Analyst focuses on collecting, analyzing, and interpreting data related to cyber threats, attackers, and their techniques. They provide actionable insights to enhance an organization’s cybersecurity strategy and threat detection capabilities.
The average salary for this role ranges from $90,000 to $120,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Threat Intelligence Analyst (CTIA). The job process involves threat data collection, analysis, reporting, intelligence sharing, and collaboration with incident response teams.
Example Job Process:
- Threat Data Collection: Gather information from open sources, dark web, and internal telemetry.
- Analysis: Analyze threat data to identify patterns, tactics, techniques, and indicators of compromise (IOCs).
- Reporting: Produce threat intelligence reports to inform decision-making and incident response.
- Intelligence Sharing: Share threat insights with industry partners and threat intelligence communities.
- Incident Response Collaboration: Collaborate with incident response teams to refine threat detection and response strategies.
37. Cybersecurity Risk Analyst:
A Cybersecurity Risk Analyst assesses an organization’s risk landscape by evaluating vulnerabilities, threats, and potential impacts. They help prioritize security efforts by identifying critical areas that require mitigation. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Risk and Information Systems Control (CRISC). The job process involves risk assessment, impact analysis, risk treatment planning, risk monitoring, and reporting to leadership.
Example Job Process:
Risk Assessment: Identify assets, vulnerabilities, and potential threats to the organization. Impact Analysis: Evaluate the potential consequences of realized threats and vulnerabilities. Risk Treatment Planning: Develop strategies to mitigate, transfer, or accept identified risks.
Risk Monitoring: Continuously monitor the risk landscape for emerging threats and changes. Leadership Reporting: Communicate risk findings, treatments, and recommendations to leadership.
38. Cybersecurity Incident Responder:
A Cybersecurity Incident Responder focuses on detecting, containing, and mitigating cybersecurity incidents, such as breaches and attacks. They work swiftly to minimize damage, investigate root causes, and restore normal operations. The average salary for this role ranges from $90,000 to $120,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Incident Handler (CIH). The job process involves incident detection, triage, containment, investigation, eradication, recovery, and post-incident analysis.
Example Job Process:
- Incident Detection: Monitor systems for signs of unauthorized access, malware, or anomalies.
- Triage: Assess incidents to determine their severity and potential impact.
- Containment: Isolate affected systems to prevent further spread of the attack.
- Investigation: Analyze the attack vector, tactics, techniques, and indicators of compromise (IOCs).
- Eradication and Recovery: Remove malicious components and restore systems to a secure state.
- Post-Incident Analysis: Conduct post-mortem analysis to understand lessons learned and improve incident response.
39. Cybersecurity Governance Specialist:
A Cybersecurity Governance Specialist focuses on establishing and maintaining effective governance frameworks for cybersecurity programs. They ensure that cybersecurity activities align with organizational objectives and regulatory requirements. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves policy development, compliance monitoring, risk assessment, reporting, and collaboration with stakeholders.
Example Job Process:
- Policy Development: Create cybersecurity policies that reflect industry standards and regulations.
- Compliance Monitoring: Monitor adherence to policies, standards, and regulatory requirements.
- Risk Assessment: Identify cybersecurity risks and prioritize them based on potential impact.
- Reporting: Generate reports to provide insights into the organization’s cybersecurity posture.
- Stakeholder Collaboration: Collaborate with various departments to ensure alignment with cybersecurity objectives.
40. Security Automation Engineer:
A Security Automation Engineer focuses on developing and implementing automated solutions to enhance security operations and response efficiency. They create scripts, tools, and workflows that streamline repetitive tasks and improve incident response times.
The average salary for this role ranges from $90,000 to $120,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Cloud Security Professional (CCSP).
The job process involves identifying automation opportunities, script development, tool integration, continuous improvement, and collaboration with security teams.
Example Job Process:
- Automation Opportunities: Identify tasks and processes that can be automated to improve efficiency.
- Script Development: Create scripts and code snippets to perform automated security tasks.
- Tool Integration: Integrate automation scripts with security tools and systems for seamless operation.
- Continuous Improvement: Monitor and optimize automated workflows for effectiveness and accuracy.
- Collaboration: Work closely with security teams to identify new automation needs and solutions.
These roles demonstrate the wide range of opportunities within the cybersecurity field. From threat intelligence analysis and risk assessment to incident response, governance, and security automation, each role contributes to enhancing cybersecurity measures and protecting digital assets in an ever-evolving threat landscape.
41. Malware Analyst:
A Malware Analyst specializes in dissecting and analyzing malicious software to understand its behavior, functionality, and potential impact. They play a critical role in identifying new malware strains and developing countermeasures. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Malware Investigator (CMI). The job process involves malware sample collection, analysis, reverse engineering, creating signatures, and collaborating with threat intelligence teams.
Example Job Process:
Malware Sample Collection: Gather malware samples from various sources, such as network logs or email attachments.
Analysis: Investigate the malware’s functionality, communication patterns, and potential payloads.
Reverse Engineering: Reverse engineer the malware code to understand its structure and behavior.
Signature Creation: Develop signatures and detection mechanisms to identify and block malware.
Threat Intelligence Collaboration: Share findings with threat intelligence teams to enhance collective knowledge.
42. Cybersecurity Sales Engineer:
A Cybersecurity Sales Engineer combines technical expertise with sales skills to communicate the value of cybersecurity solutions to clients. They understand clients’ security needs, tailor solutions, and assist in the sales process. The average salary for this role ranges from $90,000 to $120,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves client needs analysis, solution design, technical presentations, product demonstrations, and post-sale support.
Example Job Process:
- Client Needs Analysis: Understand clients’ security challenges and requirements.
- Solution Design: Recommend and tailor cybersecurity solutions to address specific needs.
- Technical Presentations: Deliver presentations that explain the technical features and benefits of solutions.
- Product Demonstrations: Demonstrate how cybersecurity solutions work in real-world scenarios.
- Post-Sale Support: Provide technical support to clients after solutions are implemented.
43. Cryptographer:
A Cryptographer focuses on designing secure cryptographic systems to protect sensitive information and communications. They create algorithms, protocols, and encryption methods that withstand attacks. The average salary for this role ranges from $100,000 to $130,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Cryptography Professional (CCP). The job process involves algorithm design, security analysis, implementation, testing, and collaboration with software developers.
Example Job Process:
- Algorithm Design: Create cryptographic algorithms that provide confidentiality, integrity, and authenticity.
- Security Analysis: Evaluate algorithm strength against potential attacks and vulnerabilities.
- Implementation: Implement cryptographic algorithms in software, hardware, or protocols.
- Testing: Test the algorithms for security, performance, and compatibility.
- Collaboration with Developers: Work with developers to integrate cryptographic solutions into applications and systems.
44. Cybersecurity Forensic Analyst:
A Cybersecurity Forensic Analyst specializes in collecting, preserving, and analyzing digital evidence to investigate cybercrimes and security incidents. They play a vital role in legal proceedings and incident response. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Digital Forensics Examiner (CDFE). The job process involves evidence collection, preservation, analysis, reporting, and courtroom testimony.
Example Job Process:
Evidence Collection: Gather digital evidence from computers, networks, and storage devices.
Preservation: Ensure the integrity of evidence through proper handling and preservation.
Analysis: Analyze digital artifacts, logs, and files to reconstruct events and timelines.
Reporting: Generate detailed reports that present findings and support investigations.
Courtroom Testimony: Provide expert testimony in legal proceedings based on forensic findings.
45. Security Architect:
A Security Architect designs and oversees the implementation of secure systems, applications, and infrastructure. They ensure that security controls are integrated into every aspect of an organization’s technology environment. The average salary for this role ranges from $120,000 to $150,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Security Architecture Professional (CISSP-ISSAP). The job process involves security design, architecture review, risk assessment, technology evaluation, and collaboration with development and operations teams.
Example Job Process:
- Security Design: Develop security architectures that align with business goals and compliance requirements.
- Architecture Review: Review existing system architectures for security weaknesses and improvements.
- Risk Assessment: Identify security risks and recommend risk mitigation strategies.
- Technology Evaluation: Evaluate new technologies for security implications and suitability.
- Collaboration: Collaborate with development and operations teams to implement secure solutions.
These roles illustrate the diverse opportunities within the cybersecurity field. From malware analysis and cryptography to sales engineering, forensics, and security architecture, each role contributes to the overarching goal of safeguarding digital assets, data, and systems in an increasingly connected world.
46. Industrial Control Systems (ICS) Security Analyst:
An ICS Security Analyst focuses on securing critical infrastructure systems, such as those used in manufacturing, energy, and utilities. They assess vulnerabilities, monitor for threats, and implement safeguards to protect industrial environments from cyberattacks.
The average salary for this role ranges from $90,000 to $120,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Industrial Cybersecurity Professional (CICSP). The job process involves ICS risk assessment, vulnerability management, incident response planning, and collaboration with operational teams.
Example Job Process:
- ICS Risk Assessment: Identify risks and vulnerabilities in industrial control systems.
- Vulnerability Management: Monitor for security vulnerabilities and apply patches and updates.
- Incident Response Planning: Develop strategies to respond to cybersecurity incidents in industrial environments.
- Collaboration with Operational Teams: Work closely with operational teams to implement security measures without disrupting critical processes.
47. Security Data Scientist:
A Security Data Scientist leverages data analysis, machine learning, and artificial intelligence to detect patterns, anomalies, and potential security threats within large datasets. They contribute to developing advanced analytics for threat detection and response.
The average salary for this role ranges from $100,000 to $130,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Data Science Professional (CDSP).
The job process involves data collection, analysis, model development, threat detection, and collaboration with data engineering teams.
Example Job Process:
- Data Collection: Collect and preprocess large datasets containing security-related information.
- Analysis: Use data analysis techniques to identify patterns and anomalies that could indicate security threats.
- Model Development: Build machine learning models for threat detection and predictive analytics.
- Threat Detection: Implement models to detect potential security threats in real-time data.
- Collaboration: Work with data engineering teams to ensure data quality and accessibility.
48. Cybersecurity Compliance Analyst:
A Cybersecurity Compliance Analyst ensures that an organization’s security practices align with relevant regulatory requirements and industry standards. They monitor compliance, perform audits, and implement measures to maintain conformity. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Auditor (CISA). The job process involves compliance assessment, policy enforcement, audit preparation, remediation planning, and communication with regulatory bodies.
Example Job Process:
- Compliance Assessment: Evaluate the organization’s security practices against relevant regulations and standards.
- Policy Enforcement: Ensure adherence to established security policies and procedures.
- Audit Preparation: Prepare for internal and external audits by gathering evidence and documentation.
- Remediation Planning: Develop plans to address identified compliance gaps and vulnerabilities.
- Communication with Regulatory Bodies: Interact with regulatory authorities to report compliance status and respond to inquiries.
49. Cybersecurity Business Continuity Planner:
A Cybersecurity Business Continuity Planner focuses on ensuring an organization’s ability to maintain essential functions during and after a cybersecurity incident or disaster. They develop strategies, plans, and processes to ensure business resilience.
The average salary for this role ranges from $90,000 to $120,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Business Continuity Professional (CBCP).
The job process involves risk assessment, continuity planning, plan testing, incident response coordination, and communication with stakeholders.
Example Job Process:
- Risk Assessment: Identify cybersecurity risks that could disrupt business operations.
- Continuity Planning: Develop comprehensive business continuity plans that address cybersecurity incidents.
- Plan Testing: Conduct regular testing and drills to ensure the effectiveness of continuity plans.
- Incident Response Coordination: Coordinate with incident response teams to activate continuity plans when needed.
- Stakeholder Communication: Communicate with stakeholders, including employees, customers, and vendors, about business continuity measures.
50. Cybersecurity Product Manager:
A Cybersecurity Product Manager is responsible for the development and management of cybersecurity products and solutions. They work closely with development teams, marketing, and customers to ensure that products meet security needs and market demands. The average salary for this role ranges from $100,000 to $130,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Product Manager (CPM). The job process involves market research, product roadmap creation, feature prioritization, development coordination, and customer feedback incorporation.
Example Job Process:
- Market Research: Analyze market trends, customer needs, and competitive offerings.
- Product Roadmap: Create a strategic plan outlining the development and launch of cybersecurity products.
- Feature Prioritization: Determine the most valuable features to be included in the product.
- Development Coordination: Work closely with development teams to ensure the timely and high-quality delivery of features.
- Customer Feedback Incorporation: Gather and incorporate customer feedback to improve product functionality and user experience.
These roles demonstrate the diverse and evolving nature of cybersecurity careers. From securing critical infrastructure to harnessing data analytics, managing compliance, ensuring business continuity, and leading product development, professionals in these roles contribute to the protection and advancement of cybersecurity practices in a rapidly changing digital landscape.
51. Cybersecurity Operations Manager:
A Cybersecurity Operations Manager oversees the daily activities of a security operations center (SOC) or a cybersecurity team. They ensure the effectiveness of security measures, incident response processes, and ongoing monitoring. The average salary for this role ranges from $110,000 to $140,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves team management, incident response coordination, security tool optimization, metrics analysis, and reporting.
Example Job Process:
- Team Management: Lead and manage a team of security analysts, incident responders, and engineers.
- Incident Response Coordination: Oversee the response to security incidents, ensuring effective containment and recovery.
- Security Tool Optimization: Optimize the configuration and usage of security tools for accurate threat detection.
- Metrics Analysis: Analyze metrics and key performance indicators (KPIs) to measure the effectiveness of security operations.
- Reporting: Generate reports for senior management to communicate security posture, incidents, and improvements.
52. Cybersecurity Trainer:
A Cybersecurity Trainer designs and delivers training programs to educate individuals and teams about cybersecurity best practices, policies, and skills. They play a crucial role in building a security-conscious culture within organizations.
The average salary for this role ranges from $80,000 to $110,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves curriculum development, training delivery, skill assessment, feedback incorporation, and continuous improvement.
Example Job Process:
- Curriculum Development: Create engaging training materials, modules, and exercises.
- Training Delivery: Conduct interactive training sessions on cybersecurity topics.
- Skill Assessment: Evaluate participants’ understanding through assessments and practical exercises.
- Feedback Incorporation: Incorporate feedback to enhance training content and delivery methods.
- Continuous Improvement: Stay updated with evolving threats and technologies to refine training programs.
53. Cybersecurity Policy Analyst:
A Cybersecurity Policy Analyst focuses on developing, reviewing, and implementing cybersecurity policies and procedures that align with industry standards and regulations. They ensure organizations maintain compliance and adhere to best practices. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves policy research, drafting, review, implementation planning, and ongoing policy management.
Example Job Process:
- Policy Research: Stay informed about evolving cybersecurity regulations, standards, and best practices.
- Policy Drafting: Develop comprehensive cybersecurity policies tailored to the organization’s needs.
- Review and Approval: Collaborate with stakeholders to review and gain approval for policies.
- Implementation Planning: Develop strategies to ensure policies are effectively communicated and enforced.
- Ongoing Policy Management: Continuously update and refine policies to adapt to changing threats and requirements.
54. Cybersecurity Auditor:
A Cybersecurity Auditor evaluates an organization’s security controls, practices, and processes to ensure compliance with regulatory requirements and industry standards. They conduct thorough assessments to identify gaps and recommend improvements.
The average salary for this role ranges from $90,000 to $120,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Auditor (CISA).
The job process involves audit planning, control assessment, findings analysis, report generation, and collaboration with stakeholders for remediation.
Example Job Process:
- Audit Planning: Define the scope, objectives, and methodologies for cybersecurity audits.
- Control Assessment: Evaluate security controls, policies, and procedures against standards.
- Findings Analysis: Identify vulnerabilities, weaknesses, and areas of non-compliance.
- Report Generation: Document findings, risks, and recommendations in audit reports.
- Remediation Collaboration: Work with stakeholders to address audit findings and enhance controls.
55. Cybersecurity Incident Responder:
A Cybersecurity Incident Responder focuses on detecting, containing, and mitigating cybersecurity incidents, such as breaches and attacks. They work swiftly to minimize damage, investigate root causes, and restore normal operations. The average salary for this role ranges from $90,000 to $120,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Incident Handler (CIH). The job process involves incident detection, triage, containment, investigation, eradication, recovery, and post-incident analysis.
Example Job Process:
- Incident Detection: Monitor systems for signs of unauthorized access, malware, or anomalies.
- Triage: Assess incidents to determine their severity and potential impact.
- Containment: Isolate affected systems to prevent further spread of the attack.
- Investigation: Analyze the attack vector, tactics, techniques, and indicators of compromise (IOCs).
- Eradication and Recovery: Remove malicious components and restore systems to a secure state.
- Post-Incident Analysis: Conduct post-mortem analysis to understand lessons learned and improve incident response.
These roles showcase the diverse responsibilities and opportunities within the cybersecurity landscape. Whether it’s managing security operations, training personnel, developing policies, conducting audits, or responding to incidents, these professionals contribute to the overarching goal of maintaining a secure digital environment.
56. Cybersecurity Data Privacy Analyst:
A Cybersecurity Data Privacy Analyst specializes in ensuring the protection and privacy of sensitive information, in accordance with data protection regulations such as GDPR or HIPAA. They assess data handling practices, develop privacy policies, and implement measures to safeguard personal data.
The average salary for this role ranges from $80,000 to $110,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Privacy Professional (CIPP). The job process involves data privacy assessment, policy development, compliance monitoring, incident response, and user education.
Example Job Process:
- Data Privacy Assessment: Evaluate how personal data is collected, processed, and stored.
- Policy Development: Create data privacy policies that align with relevant regulations.
- Compliance Monitoring: Monitor adherence to data protection regulations and policies.
- Incident Response: Develop procedures for responding to data breaches and privacy incidents.
- User Education: Educate employees and users on data privacy best practices and policies.
57. Cybersecurity Business Analyst:
A Cybersecurity Business Analyst bridges the gap between cybersecurity teams and business stakeholders. They translate business requirements into cybersecurity solutions, ensuring that security measures align with business objectives. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Security Architecture Professional (CISSP-ISSAP). The job process involves requirements gathering, solution design, communication with stakeholders, project coordination, and risk assessment.
Example Job Process:
Requirements Gathering: Collaborate with business units to identify cybersecurity needs and objectives.
Solution Design: Translate business requirements into technical cybersecurity solutions.
Communication with Stakeholders: Communicate proposed solutions, benefits, and risks to stakeholders.
Project Coordination: Work with cybersecurity teams to implement solutions within project timelines.
Risk Assessment: Evaluate potential risks and impacts of proposed solutions on business operations.
58. Red Teamer / Penetration Tester:
A Red Teamer or Penetration Tester simulates real-world cyberattacks to identify vulnerabilities and weaknesses in an organization’s systems, networks, and applications. They help organizations understand their security posture and improve defenses.
The average salary for this role ranges from $90,000 to $120,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Ethical Hacker (CEH). The job process involves scope definition, vulnerability analysis, exploitation, report generation, and collaboration with blue teams.
Example Job Process:
Scope Definition: Define the scope and rules of engagement for the penetration test. Vulnerability Analysis: Identify potential vulnerabilities through reconnaissance and scanning. Exploitation: Attempt to exploit identified vulnerabilities to gain unauthorized access.
Report Generation: Document findings, including vulnerabilities, attack paths, and recommendations. Collaboration with Blue Teams: Work with defensive teams to improve security based on test results.
59. Cybersecurity Operations Analyst:
A Cybersecurity Operations Analyst monitors and analyzes security events and incidents to detect and respond to threats in real-time. They play a critical role in maintaining a strong security posture. The average salary for this role ranges from $70,000 to $100,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and CompTIA Security+. The job process involves real-time monitoring, event analysis, incident detection, escalation, and collaboration with incident response teams.
Example Job Process:
- Real-Time Monitoring: Monitor security events from various sources, such as SIEM tools.
- Event Analysis: Analyze event data to identify patterns and potential security incidents.
- Incident Detection: Detect and classify security incidents based on predefined criteria.
- Escalation: Escalate confirmed incidents to incident response teams for further investigation.
- Incident Response Collaboration: Collaborate with incident response teams to address and mitigate threats.
60. Cybersecurity Policy Manager:
A Cybersecurity Policy Manager oversees the development, implementation, and enforcement of cybersecurity policies and procedures across an organization. They ensure that security practices align with industry standards and regulations. The average salary for this role ranges from $90,000 to $120,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves policy development, compliance tracking, policy enforcement, risk assessment, and collaboration with stakeholders.
Example Job Process:
- Policy Development: Create comprehensive cybersecurity policies and procedures.
- Compliance Tracking: Monitor adherence to established policies and regulatory requirements.
- Policy Enforcement: Ensure that security policies are communicated and enforced effectively.
- Risk Assessment: Identify risks associated with policy non-compliance and recommend mitigation strategies.
- Stakeholder Collaboration: Collaborate with various departments to align security policies with organizational objectives.
- These roles underscore the vast array of opportunities within the cybersecurity field. From data privacy and business analysis to penetration testing, operations monitoring, and policy management, each role contributes to the overarching goal of securing digital assets and information in an ever-evolving threat landscape.
61. Cybersecurity Governance Manager:
A Cybersecurity Governance Manager oversees the establishment and maintenance of cybersecurity governance frameworks within an organization. They ensure that security initiatives align with business goals, regulatory requirements, and industry standards.
The average salary for this role ranges from $100,000 to $130,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM).
The job process involves governance framework design, policy creation, risk assessment, compliance monitoring, and reporting to leadership.
Example Job Process:
- Governance Framework Design: Develop a comprehensive governance framework that guides cybersecurity activities.
- Policy Creation: Draft cybersecurity policies and standards that align with regulatory requirements.
- Risk Assessment: Identify cybersecurity risks and prioritize them based on potential impact.
- Compliance Monitoring: Monitor adherence to policies and regulatory requirements.
- Leadership Reporting: Communicate cybersecurity posture, risks, and improvements to leadership.
62. Cybersecurity Ethics Consultant:
A Cybersecurity Ethics Consultant focuses on the ethical implications of cybersecurity practices and technologies. They assess the ethical considerations of security measures and ensure that cybersecurity decisions align with ethical standards. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Ethical Hacker (CEH). The job process involves ethical analysis, policy development, stakeholder engagement, and incorporation of ethical considerations into cybersecurity strategies.
Example Job Process:
Ethical Analysis: Evaluate the potential ethical implications of cybersecurity decisions.
Policy Development: Develop guidelines and policies that ensure ethical cybersecurity practices.
Stakeholder Engagement: Collaborate with stakeholders to gather perspectives on ethical concerns.
Incorporating Ethical Considerations: Integrate ethical considerations into cybersecurity strategies, technologies, and policies.
63. Threat Hunting Analyst:
A Threat Hunting Analyst proactively searches for signs of advanced threats and hidden attackers within an organization’s networks and systems. They use data analysis and threat intelligence to identify potential security breaches. The average salary for this role ranges from $90,000 to $120,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Threat Hunter (CTH). The job process involves threat hunting planning, data analysis, indicator identification, incident response coordination, and collaboration with threat intelligence teams.
Example Job Process:
- Threat Hunting Planning: Plan and prioritize proactive threat hunting activities.
- Data Analysis: Analyze network and system data to identify unusual patterns and behaviors.
- Indicator Identification: Identify potential indicators of compromise (IOCs) and attack techniques.
- Incident Response Coordination: Collaborate with incident response teams to mitigate identified threats.
- Threat Intelligence Collaboration: Share findings and collaborate with threat intelligence teams to enhance knowledge.
64. Cybersecurity AI/Machine Learning Engineer:
A Cybersecurity AI/Machine Learning Engineer focuses on developing and implementing artificial intelligence and machine learning solutions for cybersecurity applications. They build models to detect threats, automate responses, and enhance security analytics. The average salary for this role ranges from $100,000 to $130,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Machine Learning Professional (CMLP). The job process involves data preprocessing, model development, training, validation, integration, and ongoing refinement.
Example Job Process:
- Data Preprocessing: Prepare and clean datasets for machine learning applications.
- Model Development: Build machine learning models to detect threats and anomalies.
- Training and Validation: Train models using labeled data and validate their performance.
- Integration: Integrate machine learning solutions into security systems and processes.
- Ongoing Refinement: Continuously monitor and improve model performance and accuracy.
65. Cybersecurity Incident Coordinator:
A Cybersecurity Incident Coordinator is responsible for managing and coordinating the response to cybersecurity incidents across an organization. They ensure that all incident response efforts are well-organized and effective.
The average salary for this role ranges from $90,000 to $120,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Incident Handler (CIH).
The job process involves incident identification, team coordination, communication, mitigation, documentation, and post-incident analysis.
Example Job Process:
- Incident Identification: Identify and classify cybersecurity incidents based on predefined criteria.
- Team Coordination: Coordinate incident response efforts among different teams.
- Communication: Keep stakeholders informed about incident progress, actions, and outcomes.
- Mitigation: Oversee the implementation of measures to contain and eradicate threats.
- Documentation: Document incident details, response actions, and lessons learned.
Post-Incident Analysis: Analyze the incident response process to identify areas for improvement.
These roles exemplify the diverse and dynamic nature of careers in the cybersecurity field. From governance and ethics to threat hunting, AI-driven security, and incident coordination, each role contributes to the overarching goal of safeguarding digital assets, privacy, and information in today’s complex and interconnected landscape.
66. Cybersecurity Compliance Manager:
A Cybersecurity Compliance Manager is responsible for ensuring that an organization’s cybersecurity practices align with relevant regulations, industry standards, and internal policies. They oversee compliance assessments, audits, and reporting.
The average salary for this role ranges from $100,000 to $130,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM).
The job process involves compliance tracking, policy enforcement, audit preparation, findings remediation, and collaboration with regulatory bodies.
Example Job Process:
- Compliance Tracking: Monitor adherence to cybersecurity regulations and standards.
- Policy Enforcement: Ensure that security policies and practices align with compliance requirements.
- Audit Preparation: Prepare for internal and external audits by gathering evidence and documentation.
- Findings Remediation: Address compliance gaps and vulnerabilities identified during audits.
- Collaboration with Regulatory Bodies: Interact with regulatory authorities to report compliance status and respond to inquiries.
67. Cybersecurity Business Continuity Analyst:
A Cybersecurity Business Continuity Analyst focuses on developing and implementing strategies to ensure the continuity of business operations in the face of cybersecurity incidents or disasters. They contribute to the organization’s resilience. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Business Continuity Professional (CBCP). The job process involves risk assessment, continuity planning, disaster recovery coordination, training, and testing.
Example Job Process:
- Risk Assessment: Identify potential cybersecurity risks and their impact on business operations.
- Continuity Planning: Develop comprehensive business continuity plans that address cybersecurity incidents.
- Disaster Recovery Coordination: Coordinate disaster recovery efforts to restore critical systems and data.
- Training: Train employees on business continuity procedures and their roles during incidents.
- Testing: Conduct regular testing and drills to validate the effectiveness of business continuity plans.
68. Cybersecurity Vendor Risk Manager:
A Cybersecurity Vendor Risk Manager assesses and manages the cybersecurity risks associated with third-party vendors and partners. They ensure that vendors meet security standards and protect the organization’s interests. The average salary for this role ranges from $90,000 to $120,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Third-Party Risk Professional (CTPRP). The job process involves risk assessment, vendor evaluation, contract negotiation, monitoring, and incident response planning.
Example Job Process:
- Risk Assessment: Evaluate the cybersecurity risks posed by third-party vendors.
- Vendor Evaluation: Assess vendor security controls, policies, and practices.
- Contract Negotiation: Include cybersecurity requirements in vendor contracts and agreements.
- Monitoring: Continuously monitor vendor compliance with security standards.
- Incident Response Planning: Develop strategies for responding to cybersecurity incidents involving vendors.
69. Cybersecurity Incident Communication Specialist:
A Cybersecurity Incident Communication Specialist is responsible for managing external and internal communication during cybersecurity incidents. They ensure that accurate information is shared with stakeholders and the public.
The average salary for this role ranges from $80,000 to $110,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Communication Security Professional (CCSP).
The job process involves communication planning, message development, media relations, stakeholder updates, and crisis communication management.
Example Job Process:
- Communication Planning: Develop a communication strategy for different stages of cybersecurity incidents.
- Message Development: Craft accurate and transparent messages for stakeholders and the public.
- Media Relations: Coordinate communication with media outlets to provide accurate information.
- Stakeholder Updates: Keep internal and external stakeholders informed about incident developments.
- Crisis Communication Management: Manage communication challenges and misinformation during incidents.
70. Cybersecurity Compliance Analyst:
A Cybersecurity Compliance Analyst ensures that an organization’s security practices comply with relevant regulations, industry standards, and internal policies. They assess vulnerabilities and monitor compliance efforts. The average salary for this role ranges from $70,000 to $100,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Auditor (CISA). The job process involves compliance assessment, policy enforcement, audit preparation, findings remediation, and collaboration with compliance teams.
Example Job Process:
- Compliance Assessment: Evaluate the organization’s cybersecurity practices against relevant regulations and standards.
- Policy Enforcement: Ensure that security policies and practices align with compliance requirements.
- Audit Preparation: Prepare for internal and external audits by gathering evidence and documentation.
- Findings Remediation: Address compliance gaps and vulnerabilities identified during audits.
- Collaboration with Compliance Teams: Work with compliance teams to align cybersecurity practices with regulatory requirements.
These roles continue to showcase the rich variety of career paths within the cybersecurity realm. From compliance management and incident communication to vendor risk assessment and business continuity, each role plays a pivotal role in strengthening cybersecurity strategies and mitigating risks in today’s complex digital landscape.
71. Cybersecurity Policy Analyst:
A Cybersecurity Policy Analyst is responsible for developing, reviewing, and implementing cybersecurity policies and procedures that align with industry standards and regulations. They ensure organizations maintain compliance and adhere to best practices.
The average salary for this role ranges from $80,000 to $110,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Security Architecture Professional (CISSP-ISSAP). The job process involves policy research, drafting, review, implementation planning, and ongoing policy management.
Example Job Process:
Policy Research: Stay informed about evolving cybersecurity regulations, standards, and best practices.
Policy Drafting: Develop comprehensive cybersecurity policies tailored to the organization’s needs.
Review and Approval: Collaborate with stakeholders to review and gain approval for policies.
Implementation Planning: Develop strategies to ensure policies are effectively communicated and enforced.
Ongoing Policy Management: Continuously update and refine policies to adapt to changing threats and requirements.
72. Security Automation Engineer:
A Security Automation Engineer focuses on automating cybersecurity tasks and processes to improve efficiency and reduce human error. They develop scripts, tools, and workflows that enhance security operations. The average salary for this role ranges from $90,000 to $120,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Cloud Security Professional (CCSP). The job process involves identifying automation opportunities, script development, integration, testing, and maintenance.
Example Job Process:
- Identify Automation Opportunities: Identify repetitive tasks in security operations that can be automated.
- Script Development: Develop scripts and tools to automate tasks such as log analysis, vulnerability scanning, and incident response.
- Integration: Integrate automation solutions with existing security tools and systems.
- Testing: Test automation scripts and tools to ensure accuracy and reliability.
- Maintenance: Monitor and maintain automation solutions, making updates as needed.
73. Cybersecurity Researcher:
A Cybersecurity Researcher conducts in-depth research to understand emerging threats, vulnerabilities, and attack techniques. They contribute to the development of new security solutions and strategies. The average salary for this role ranges from $90,000 to $120,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and CompTIA Security+. The job process involves threat research, vulnerability analysis, experiment design, data collection, and collaboration with security teams.
Example Job Process:
- Threat Research: Stay updated on the latest cybersecurity threats and attack techniques.
- Vulnerability Analysis: Identify vulnerabilities in software, systems, and networks.
- Experiment Design: Design controlled experiments to understand how threats and vulnerabilities work.
- Data Collection: Gather data to analyze and draw conclusions about potential risks.
- Collaboration with Security Teams: Share findings and collaborate with security teams to develop countermeasures.
74. Cybersecurity Sales Engineer:
A Cybersecurity Sales Engineer combines technical expertise with sales skills to help customers understand and implement cybersecurity solutions. They provide technical demonstrations, answer technical questions, and assist in solution design. The average salary for this role ranges from $100,000 to $130,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Security Architecture Professional (CISSP-ISSAP). The job process involves customer interactions, solution presentation, technical consultation, proposal development, and post-sales support.
Example Job Process:
- Customer Interactions: Engage with customers to understand their cybersecurity needs and challenges.
- Solution Presentation: Demonstrate how cybersecurity solutions can address specific customer requirements.
- Technical Consultation: Provide expert guidance on the implementation and use of security products.
- Proposal Development: Collaborate with sales teams to create proposals that outline technical solutions.
- Post-Sales Support: Assist customers with product implementation, troubleshooting, and ongoing support.
75. Cybersecurity UX Designer:
A Cybersecurity UX Designer focuses on creating user-friendly and secure interfaces for cybersecurity applications and tools. They prioritize usability while ensuring strong security practices. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Security Architecture Professional (CISSP-ISSAP). The job process involves user research, interface design, security integration, usability testing, and continuous improvement.
Example Job Process:
- User Research: Gather insights from users to understand their needs and preferences.
- Interface Design: Create intuitive and visually appealing user interfaces for security applications.
- Security Integration: Integrate security features and controls into the user interface design.
- Usability Testing: Conduct usability testing to ensure that security tools are easy to use.
- Continuous Improvement: Gather feedback and iteratively improve the user experience of cybersecurity applications.
These roles demonstrate the ever-expanding scope of cybersecurity careers. From policy analysis and security automation to cybersecurity research, sales engineering, and UX design, each role contributes to the development, implementation, and advancement of cybersecurity practices in a rapidly evolving digital landscape.
76. Cybersecurity Compliance Specialist:
A Cybersecurity Compliance Specialist assists in ensuring an organization’s cybersecurity practices align with relevant regulations and industry standards. They work to maintain compliance and manage documentation. The average salary for this role ranges from $70,000 to $100,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Auditor (CISA). The job process involves compliance monitoring, documentation, audit support, gap analysis, and collaboration with compliance teams.
Example Job Process:
- Compliance Monitoring: Monitor adherence to cybersecurity regulations, standards, and policies.
- Documentation: Maintain accurate records and documentation related to compliance efforts.
- Audit Support: Provide necessary documentation and information for compliance audits.
- Gap Analysis: Identify gaps between current practices and compliance requirements.
- Collaboration with Compliance Teams: Work with compliance teams to address identified gaps and enhance practices.
77. Cybersecurity Threat Intelligence Analyst:
A Cybersecurity Threat Intelligence Analyst collects, analyzes, and interprets threat data to provide actionable insights to security teams. They help organizations understand potential threats and vulnerabilities. The average salary for this role ranges from $90,000 to $120,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Threat Intelligence Analyst (CTIA). The job process involves data collection, analysis, threat profiling, information dissemination, and collaboration with security teams.
Example Job Process:
- Data Collection: Gather threat data from various sources, including threat feeds and forums.
- Analysis: Analyze threat data to identify trends, patterns, and potential risks.
- Threat Profiling: Profile threat actors and their methods to understand motivations and targets.
- Information Dissemination: Share actionable threat intelligence with security teams for mitigation.
- Collaboration with Security Teams: Collaborate with incident response and security operations teams to respond to identified threats.
78. Cybersecurity User Education Specialist:
A Cybersecurity User Education Specialist focuses on educating employees and users about cybersecurity best practices. They play a vital role in building a security-conscious culture within an organization. The average salary for this role ranges from $70,000 to $100,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Security Awareness Practitioner (CSAP). The job process involves curriculum development, training delivery, awareness campaigns, user engagement, and continuous improvement.
Example Job Process:
Curriculum Development: Develop engaging and relevant cybersecurity training materials.
Training Delivery: Conduct interactive training sessions on cybersecurity topics.
Awareness Campaigns: Design and execute campaigns to raise cybersecurity awareness.
User Engagement: Encourage user participation and engagement in security practices.
Continuous Improvement: Stay updated with evolving threats and tailor training programs accordingly.
79. Cybersecurity Incident Legal Advisor:
A Cybersecurity Incident Legal Advisor provides legal guidance during cybersecurity incidents, ensuring that organizations adhere to legal requirements while responding to incidents. They work to minimize legal risks. The average salary for this role ranges from $100,000 to $130,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Security Architecture Professional (CISSP-ISSAP).
The job process involves legal analysis, regulatory compliance, communication with legal teams, incident response coordination, and collaboration with external counsel.
Example Job Process:
- Legal Analysis: Evaluate legal implications of cybersecurity incidents and potential actions.
- Regulatory Compliance: Ensure incident response actions align with relevant regulations.
- Communication with Legal Teams: Collaborate with internal and external legal teams for advice.
- Incident Response Coordination: Work with incident response teams to address legal considerations during response.
- Collaboration with External Counsel: Engage external legal counsel when needed for specialized legal guidance.
80. Cybersecurity Operations Trainer:
A Cybersecurity Operations Trainer specializes in training security analysts and operations teams to improve their skills in monitoring, detecting, and responding to cybersecurity threats. They contribute to enhancing security capabilities. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Security Architecture Professional (CISSP-ISSAP). The job process involves curriculum design, training delivery, skill assessment, feedback incorporation, and continuous improvement.
Example Job Process:
Curriculum Design: Develop comprehensive training modules for cybersecurity operations teams.
Training Delivery: Deliver hands-on training sessions covering threat detection and incident response.
Skill Assessment: Evaluate participants’ skills through practical exercises and simulations.
Feedback Incorporation: Incorporate feedback to improve training content and delivery methods.
Continuous Improvement: Stay updated with emerging threats and technologies to enhance training programs.
These roles emphasize the diverse and evolving nature of careers within the cybersecurity field. From compliance management and threat intelligence to user education, legal advisory, and operations training, each role contributes to the overall goal of safeguarding digital assets and information in a dynamic and challenging cybersecurity landscape.
81. Cybersecurity Governance Analyst:
A Cybersecurity Governance Analyst plays a crucial role in establishing and maintaining effective cybersecurity governance frameworks. They ensure that an organization’s security practices align with strategic goals and regulatory requirements. The average salary for this role ranges from $70,000 to $100,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves governance framework design, policy alignment, risk assessment, compliance tracking, and reporting to leadership.
Example Job Process:
- Governance Framework Design: Develop frameworks to guide cybersecurity governance activities.
- Policy Alignment: Ensure that cybersecurity policies align with industry standards and regulations.
- Risk Assessment: Identify and assess cybersecurity risks to inform governance decisions.
- Compliance Tracking: Monitor adherence to policies and regulations, ensuring alignment.
- Leadership Reporting: Report on the organization’s cybersecurity posture, risks, and improvements to leadership.
82. Cybersecurity Threat Modeler:
A Cybersecurity Threat Modeler focuses on creating models that represent potential threats and attack scenarios to understand potential vulnerabilities. They contribute to the development of effective security strategies. The average salary for this role ranges from $90,000 to $120,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Threat Intelligence Analyst (CTIA). The job process involves threat modeling, scenario creation, analysis, risk assessment, and collaboration with security teams.
Example Job Process:
- Threat Modeling: Identify potential threats and create models that simulate attack scenarios.
- Scenario Creation: Develop realistic and detailed threat scenarios for analysis.
- Analysis: Assess the impact and likelihood of each threat scenario on security posture.
- Risk Assessment: Evaluate potential risks associated with identified vulnerabilities.
- Collaboration with Security Teams: Collaborate with security teams to develop mitigation strategies.
83. Cybersecurity Ethics Officer:
A Cybersecurity Ethics Officer focuses on ensuring that cybersecurity practices and decisions align with ethical standards. They address moral considerations in security strategies. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Ethical Hacker (CEH). The job process involves ethical analysis, policy development, employee education, stakeholder engagement, and incorporation of ethical considerations into security strategies.
Example Job Process:
Ethical Analysis: Evaluate potential ethical implications of cybersecurity practices and decisions.
Policy Development: Develop guidelines and policies that ensure ethical cybersecurity practices.
Employee Education: Train employees on ethical considerations in cybersecurity decision-making.
Stakeholder Engagement: Collaborate with stakeholders to gather input on ethical concerns.
Incorporating Ethical Considerations: Integrate ethical considerations into cybersecurity strategies and practices.
84. Cybersecurity Product Manager:
A Cybersecurity Product Manager is responsible for the development, enhancement, and management of cybersecurity products and solutions. They bridge the gap between technical teams and business goals. The average salary for this role ranges from $100,000 to $130,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves product roadmap planning, feature definition, stakeholder communication, development coordination, and product launch.
Example Job Process:
- Product Roadmap Planning: Define the long-term vision and strategy for cybersecurity products.
- Feature Definition: Gather requirements and define features based on customer needs and market trends.
- Stakeholder Communication: Communicate product plans, updates, and milestones to stakeholders.
- Development Coordination: Collaborate with development teams to ensure timely product delivery.
- Product Launch: Oversee the successful launch of cybersecurity products in the market.
85. Cybersecurity Operations Coordinator:
A Cybersecurity Operations Coordinator supports the coordination and execution of cybersecurity operations activities. They ensure that security operations run smoothly and efficiently. The average salary for this role ranges from $70,000 to $100,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and CompTIA Security+. The job process involves operations planning, task assignment, communication, incident response coordination, and collaboration with security teams.
Example Job Process:
Operations Planning: Plan and schedule cybersecurity operations tasks and activities.
Task Assignment: Assign responsibilities and tasks to security operations team members.
Communication: Keep team members informed about task assignments and objectives.
Incident Response Coordination: Coordinate incident response efforts across the security operations team.
Collaboration with Security Teams: Collaborate with other security teams to address emerging threats and incidents.
86. Cybersecurity Forensic Analyst:
A Cybersecurity Forensic Analyst specializes in investigating and analyzing cybersecurity incidents to collect evidence, identify the scope of breaches, and aid in legal proceedings. They play a crucial role in incident response. The average salary for this role ranges from $90,000 to $120,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Computer Hacking Forensic Investigator (CHFI). The job process involves evidence collection, analysis, report generation, legal support, and collaboration with incident response teams.
Example Job Process:
- Evidence Collection: Collect and preserve digital evidence related to cybersecurity incidents.
- Analysis: Analyze evidence to understand the scope and impact of security breaches.
- Report Generation: Generate detailed reports on findings, methods, and evidence.
- Legal Support: Provide support and expertise in legal proceedings related to cybersecurity incidents.
- Collaboration with Incident Response Teams: Collaborate with incident response teams to develop effective strategies.
87. Cybersecurity Data Scientist:
A Cybersecurity Data Scientist leverages data analysis and machine learning techniques to identify patterns, trends, and anomalies in cybersecurity data. They contribute to the development of advanced threat detection methods. The average salary for this role ranges from $100,000 to $130,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Security Architecture Professional (CISSP-ISSAP). The job process involves data collection, preprocessing, analysis, model development, testing, and collaboration with security teams.
Example Job Process:
- Data Collection: Gather cybersecurity data from various sources, including logs and network traffic.
- Data Preprocessing: Clean and prepare data for analysis by removing noise and outliers.
- Analysis: Apply data analysis techniques to identify patterns and anomalies.
- Model Development: Develop machine learning models for threat detection and prediction.
- Testing: Test and validate the performance of developed models using real-world data.
- Collaboration with Security Teams: Collaborate with security teams to integrate data-driven insights into security strategies.
88. Cybersecurity Incident Recovery Specialist:
A Cybersecurity Incident Recovery Specialist focuses on post-incident recovery efforts to restore systems, data, and services affected by cybersecurity incidents. They play a critical role in minimizing downtime. The average salary for this role ranges from $80,000 to $110,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and CompTIA Security+. The job process involves recovery planning, system restoration, data retrieval, validation, and collaboration with incident response and IT teams.
Example Job Process:
- Recovery Planning: Develop detailed recovery plans outlining steps and priorities.
- System Restoration: Work to restore affected systems and services to normal operation.
- Data Retrieval: Retrieve and validate data from backups or unaffected sources.
- Validation: Test recovered systems and data to ensure functionality and integrity.
- Collaboration with Incident Response and IT Teams: Coordinate efforts with incident response and IT teams to ensure effective recovery.
89. Cybersecurity Data Privacy Specialist:
A Cybersecurity Data Privacy Specialist focuses on ensuring the privacy and protection of sensitive data in compliance with data protection regulations. They help organizations manage data privacy risks. The average salary for this role ranges from $90,000 to $120,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Privacy Professional (CIPP). The job process involves privacy assessment, policy development, data mapping, consent management, and collaboration with legal and compliance teams.
Example Job Process:
- Privacy Assessment: Evaluate the organization’s data processing activities for compliance.
- Policy Development: Develop and implement data privacy policies and procedures.
- Data Mapping: Identify and document the flow of sensitive data within the organization.
- Consent Management: Ensure that data subjects’ consents are obtained and managed appropriately.
- Collaboration with Legal and Compliance Teams: Work with legal and compliance teams to address data privacy requirements.
90. Cybersecurity Cloud Architect:
A Cybersecurity Cloud Architect specializes in designing secure cloud environments and solutions, considering best practices for cloud security. They help organizations migrate to and maintain secure cloud infrastructures. The average salary for this role ranges from $100,000 to $130,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Cloud Security Professional (CCSP). The job process involves cloud architecture design, security integration, risk assessment, compliance, and collaboration with cloud and security teams.
Example Job Process:
- Cloud Architecture Design: Design and plan secure cloud environments that align with business needs.
- Security Integration: Integrate security controls and best practices into cloud architecture.
- Risk Assessment: Evaluate potential risks associated with cloud deployments.
- Compliance: Ensure that cloud solutions meet industry-specific compliance requirements.
- Collaboration with Cloud and Security Teams: Collaborate with cloud and security teams to implement and maintain secure cloud environments.
These roles continue to highlight the diverse and dynamic opportunities within the field of cybersecurity. From governance and threat modeling to ethics, data privacy, and cloud architecture, each role contributes to the overarching goal of safeguarding digital assets and information in a complex and ever-evolving digital landscape.
91. Cybersecurity Research Scientist:
A Cybersecurity Research Scientist conducts advanced research to develop new methodologies, tools, and techniques for improving cybersecurity. They contribute to the advancement of the field through innovative solutions. The average salary for this role ranges from $120,000 to $150,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves research planning, experimentation, data analysis, solution development, and collaboration with academia and industry peers.
Example Job Process:
- Research Planning: Identify research objectives and formulate research questions.
- Experimentation: Conduct experiments to test hypotheses and gather data.
- Data Analysis: Analyze experimental data to draw conclusions and insights.
- Solution Development: Develop new tools, techniques, or methodologies based on research findings.
- Collaboration with Academia and Industry: Collaborate with academic institutions and industry peers to share findings and insights.
92. Cybersecurity Regulatory Compliance Manager:
A Cybersecurity Regulatory Compliance Manager specializes in interpreting and implementing cybersecurity regulations and compliance standards within an organization. They ensure the organization adheres to legal requirements. The average salary for this role ranges from $100,000 to $130,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Privacy Professional (CIPP). The job process involves regulatory analysis, compliance assessment, policy development, audit preparation, and collaboration with legal and compliance teams.
Example Job Process:
- Regulatory Analysis: Stay updated on evolving cybersecurity regulations and compliance standards.
- Compliance Assessment: Evaluate the organization’s adherence to regulatory requirements.
- Policy Development: Develop policies and procedures that align with regulatory guidelines.
- Audit Preparation: Prepare for compliance audits by gathering evidence and documentation.
- Collaboration with Legal and Compliance Teams: Collaborate with legal and compliance teams to address compliance gaps.
93. Cybersecurity Incident Legal Specialist:
A Cybersecurity Incident Legal Specialist combines legal expertise with cybersecurity knowledge to guide organizations through legal processes during cybersecurity incidents. They ensure compliance with laws and regulations. The average salary for this role ranges from $110,000 to $140,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Security Architecture Professional (CISSP-ISSAP). The job process involves legal analysis, incident response coordination, legal documentation, communication with legal teams, and collaboration with incident response teams.
Example Job Process:
Legal Analysis: Analyze the legal implications of cybersecurity incidents and potential actions. Incident Response Coordination: Coordinate incident response efforts while considering legal considerations. Legal Documentation: Prepare legal documents and communications related to incidents. Communication with Legal Teams: Collaborate with internal and external legal teams for guidance. Collaboration with Incident Response Teams: Work closely with incident response teams to ensure effective coordination.
94. Cybersecurity Business Continuity Planner:
A Cybersecurity Business Continuity Planner focuses on developing and maintaining strategies to ensure business continuity during cybersecurity incidents. They play a critical role in minimizing disruption. The average salary for this role ranges from $90,000 to $120,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Business Continuity Professional (CBCP). The job process involves risk assessment, continuity planning, recovery strategy development, testing, and collaboration with business units.
Example Job Process:
- Risk Assessment: Identify potential cybersecurity risks and their impact on business operations.
- Continuity Planning: Develop comprehensive business continuity plans that address cybersecurity incidents.
- Recovery Strategy Development: Define strategies for recovering critical systems and processes.
- Testing: Conduct regular tests and drills to validate the effectiveness of continuity plans.
- Collaboration with Business Units: Work with business units to ensure continuity plans align with operational needs.
95. Cybersecurity Incident Communications Manager:
A Cybersecurity Incident Communications Manager oversees communication efforts during cybersecurity incidents, ensuring accurate and timely information dissemination to stakeholders. They help manage the organization’s reputation.
The average salary for this role ranges from $100,000 to $130,000 per year. Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Communication Security Professional (CCSP).
The job process involves communication planning, message development, stakeholder updates, media relations, and collaboration with incident response teams.
Example Job Process:
- Communication Planning: Develop a communication strategy for different stages of cybersecurity incidents.
- Message Development: Craft accurate and transparent messages for stakeholders and the public.
- Stakeholder Updates: Keep internal and external stakeholders informed about incident developments.
- Media Relations: Coordinate communication with media outlets to provide accurate information.
- Collaboration with Incident Response Teams: Work closely with incident response teams to align communication efforts with incident management.
96. Cybersecurity Innovations Manager:
A Cybersecurity Innovations Manager is responsible for driving innovation within the cybersecurity field, exploring new technologies and approaches to enhance security measures. They lead research and development initiatives. The average salary for this role ranges from $110,000 to $140,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Security Architecture Professional (CISSP-ISSAP). The job process involves technology research, prototype development, innovation strategy, collaboration with research teams, and implementation of cutting-edge solutions.
Example Job Process:
- Technology Research: Identify emerging technologies and trends in the cybersecurity field.
- Prototype Development: Develop prototypes to test the feasibility and effectiveness of innovative solutions.
- Innovation Strategy: Create an innovation roadmap that aligns with business objectives.
- Collaboration with Research Teams: Collaborate with research teams to explore novel security approaches.
- Implementation of Cutting-Edge Solutions: Implement successful innovations into the organization’s cybersecurity practices.
97. Cybersecurity Incident Legal Advisor:
A Cybersecurity Incident Legal Advisor provides legal guidance during cybersecurity incidents, ensuring that organizations navigate legal complexities while responding to incidents. They safeguard the organization’s legal interests. The average salary for this role ranges from $120,000 to $150,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM). The job process involves legal analysis, regulatory compliance, communication with legal teams, incident response coordination, and collaboration with external counsel.
Example Job Process:
Legal Analysis: Evaluate the legal implications of cybersecurity incidents and potential actions.
Regulatory Compliance: Ensure incident response actions align with relevant regulations.
Communication with Legal Teams: Collaborate with internal and external legal teams for advice and guidance.
Incident Response Coordination: Work with incident response teams to address legal considerations during response.
Collaboration with External Counsel: Engage external legal counsel when specialized guidance is required.
98. Cybersecurity Product Evangelist:
A Cybersecurity Product Evangelist serves as a passionate advocate for cybersecurity products and solutions, promoting their value to customers, partners, and the industry. They play a pivotal role in driving adoption and awareness. The average salary for this role ranges from $100,000 to $130,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Security Architecture Professional (CISSP-ISSAP). The job process involves product knowledge, public speaking, content creation, engagement with stakeholders, and collaboration with marketing teams.
Example Job Process:
- Product Knowledge: Develop an in-depth understanding of cybersecurity products and their features.
- Public Speaking: Deliver compelling presentations and talks at industry events and conferences.
- Content Creation: Create informative content such as blogs, whitepapers, and videos to showcase product value.
- Engagement with Stakeholders: Interact with customers, partners, and the industry to share product insights.
- Collaboration with Marketing Teams: Collaborate with marketing teams to align product messaging and promotion strategies.
99. Cybersecurity Technology Strategist:
A Cybersecurity Technology Strategist develops and implements technology strategies that align with business goals and enhance the organization’s cybersecurity posture. They play a key role in shaping the organization’s security roadmap. The average salary for this role ranges from $120,000 to $150,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Security Architecture Professional (CISSP-ISSAP). The job process involves technology assessment, strategy development, stakeholder alignment, roadmap creation, and collaboration with technology and business teams.
Example Job Process:
Technology Assessment: Evaluate existing and emerging technologies for their potential impact on cybersecurity.
Strategy Development: Formulate technology strategies that address security challenges and support business objectives.
Stakeholder Alignment: Align technology strategies with the goals and priorities of different business units.
Roadmap Creation: Develop a comprehensive roadmap outlining the implementation of technology initiatives.
Collaboration with Technology and Business Teams: Work closely with technology and business teams to ensure successful strategy implementation.
100. Cybersecurity Data Governance Specialist:
A Cybersecurity Data Governance Specialist focuses on establishing and maintaining data governance practices to ensure the confidentiality, integrity, and availability of sensitive information. They play a critical role in data protection. The average salary for this role ranges from $110,000 to $140,000 per year.
Key certifications include Certified Information Systems Security Professional (CISSP) and Certified Information Systems Security Architecture Professional (CISSP-ISSAP). The job process involves data classification, access controls, policy development, data lifecycle management, and collaboration with data owners and compliance teams.
Example Job Process:
- Data Classification: Classify data based on its sensitivity and criticality to define appropriate protection measures.
- Access Controls: Implement access controls and permissions to ensure authorized access to data.
- Policy Development: Develop data governance policies and procedures that align with regulations.
- Data Lifecycle Management: Define processes for data creation, storage, retention, and disposal.
- Collaboration with Data Owners and Compliance Teams: Work with data owners and compliance teams to enforce data governance practices.
These diverse and specialized roles within the cybersecurity field showcase the breadth and depth of opportunities available. From research and legal advisory to business continuity planning, product evangelism, and data governance, each role contributes to the overall mission of safeguarding digital assets and information in an increasingly interconnected world.
In conclusion,
As we wrap up our journey through the world of 100 cybersecurity careers and their associated salaries, we’ve uncovered a treasure trove of opportunities that are both diverse and exciting. These jobs aren’t just about sitting behind a computer screen; they’re about being the digital defenders of our modern age.
Imagine being the hero who safeguards companies from cyber threats, the detective who uncovers vulnerabilities before they’re exploited, or the architect who designs unbreakable digital fortresses. Each role plays a unique part in maintaining the safety of our interconnected world.
But it’s not just about technical skills. It’s also about the passion and dedication these professionals bring to the table. They’re not just crunching numbers; they’re safeguarding our personal information, our financial transactions, and our digital lives. The emotional investment in these careers goes beyond just the numbers on a paycheck.
And speaking of paychecks, these careers aren’t just financially rewarding; they also offer a sense of purpose. In a world where everything is becoming digital, the demand for cybersecurity experts is skyrocketing. That means not only do these professionals get well-compensated, but they’re also securing their job stability for the future.
So, whether you’re someone who loves problem-solving, has an eye for detail, or simply wants to make a meaningful impact, the world of cybersecurity has a place for you. It’s a realm where you can learn, grow, and contribute to something bigger than yourself.
As we conclude, remember that the world of cybersecurity isn’t just for tech geniuses; it’s for anyone with a passion for protecting, exploring, and innovating in the digital landscape. So, consider this your invitation to dive in, embrace the challenges, and become a key player in the exciting world of cybersecurity.
For a comprehensive list of the top 100 Cybersecurity Jobs along with their lucrative salaries, we’ve prepared an informative infographic. You can download and print it to help guide your future career choices.